
SED
(Self-Encrypting Drive)

What Are Self-Encrypting Drives (SED)?
An SED (Self-Encrypting Drive) refers to a storage device with built-in self-encryption capabilities. It is important to clarify that an SED is not a single encryption algorithm or a specific piece of hardware IP. Rather, it is a security concept that describes a storage device’s capability to perform trusted and manageable self-encryption behaviors.
How an SED Works
From an implementation perspective, an SED typically relies on the SSD controller’s inline hardware encryption architecture. The primary differentiator lies in its support for key isolation and manageable, policy-driven access control, rather than encryption alone.
When data is written to an SSD, it is encrypted in real time by a hardware encryption engine integrated into the controller. The encrypted data (ciphertext) is then stored in NAND Flash.
Encryption keys are managed internally by the controller’s secure mechanisms and kept physically and logically separate from user data in NAND. This design ensures that even if the SSD is removed, relocated, or the host system is compromised, the data remains inaccessible without proper authentication and unlocking.
Core Capabilities of an SED
-
Inline Encryption
The foundation of an SED is the SSD controller’s built-in hardware AES encryption engine, typically utilizing the AES-256 algorithm. All data is automatically encrypted before being written to NAND and transparently decrypted when read. This entire process occurs inside the SSD, without involvement from the operating system or CPU.
Because encryption and decryption are handled by dedicated hardware in real time, performance impact is typically minimal across most workloads. In addition, the encryption process is independent of the OS, BIOS, drivers, or software updates.
It should be noted that inline encryption alone does not qualify a device as an SED. Whether a drive can be classified as an SED depends on the presence of manageable and verifiable security behaviors beyond basic encryption.
-
Device-Based Key Storage
Key isolation is the core security principle of SED architecture. In an SED, the Master Encryption Key (MEK) exists only within the Secure Zone of the SSD controller. It is never exposed to the host or any external system. This is the primary difference between an SED and pure software encryption:
.OS Corruption: If the operating system is damaged or compromised, data protection remains intact.
.Physical Theft: If the SSD is removed and connected to another computer, the data remains encrypted and inaccessible.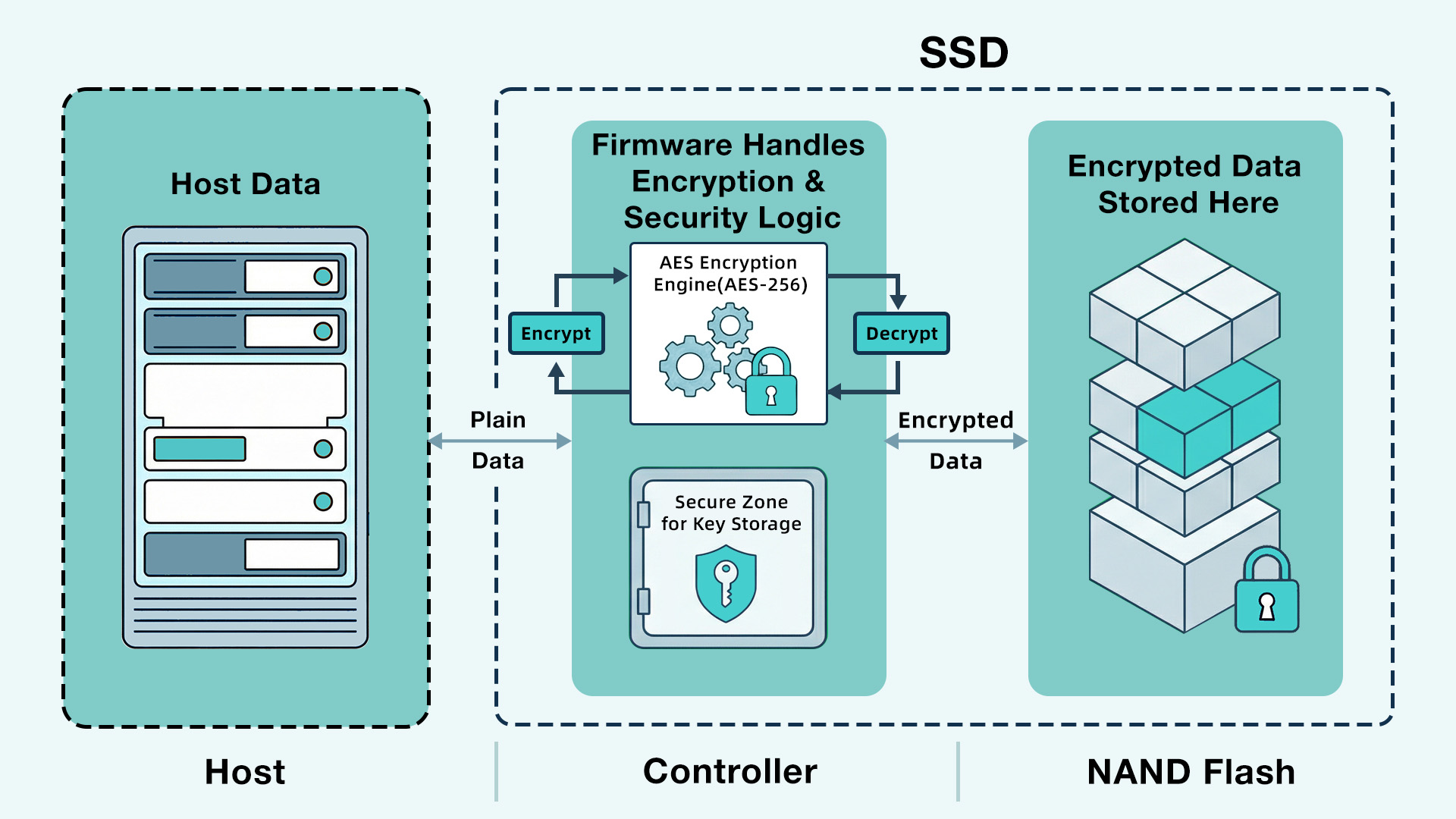
-
Instant Secure Erase, ISE
All data on an SED is stored in an encrypted state on the NAND. By performing a Key Purge, the encryption key is destroyed, rendering the remaining data permanently indecipherable—even though the ciphertext still resides in NAND. This process effectively achieves near-instantaneous cryptographic erasure of all stored data.
This key-based erase mechanism is extremely fast because it does not require overwriting the entire NAND space. It is ideal for highly security-sensitive environments, including industrial PCs, financial institutions, and government sectors, and for scenarios like server decommissioning where rapid data sanitization is required.
Depending on the interface and standard, this mechanism may be referred to by different names, including:
.Instant Secure Erase (ISE): A commonly used industry term for Enterprise SSDs.
.Crypto Erase: Terminology used in SATA / TCG specifications.
.Crypto Sanitize: The designation within NIST / NVMe Sanitize commands.
The Relationship Between SED and TCG
If SED is viewed as a security capability, the specifications defined by the Trusted Computing Group (TCG) establish how that capability is managed, verified, and access-controlled in a standardized manner.
Through standards such as TCG Opal or TCG Enterprise (TCGe), systems can apply different permission management modes based on the application scenario. For example:
- TCG Opal: Designed for client and PC environments, supporting Pre-Boot Authentication (PBA) and multi-range encryption management.
- TCGe: Optimized for data center environments with features like centralized key management and large-scale security domain control.
In essence, SED defines a storage device’s capability for manageable self-encryption, while TCG standards specify how that capability is securely implemented and managed.
(To learn more about TCG standards, please refer to the TCG article.)






__24C15hqqtC.png)
__24C15wOdCC.png)









__24C05XQ2my.jpg)






__24C05fplcZ.png)
__24C05vgHYC.png)


